When remote work took over in 2020, there was a mad dash for at-home cybersecurity. We published a checklist just for WFH risk management. But now that we’re three months away from 2022, everyone’s got in under control, right?
Not quite.
With the pandemic businesses had to adopt or die. This meant bringing entirely new technologies and processes into the mix. Video-conference software like Microsoft Teams or Zoom (sorry, Skype), new apps like Slack or Paylocity and other cloud-based tech.
With little time to train employees on best security practices, business had to learn on the go. Many are still trying to catch up. This leaves a big weakness for hackers to exploit.
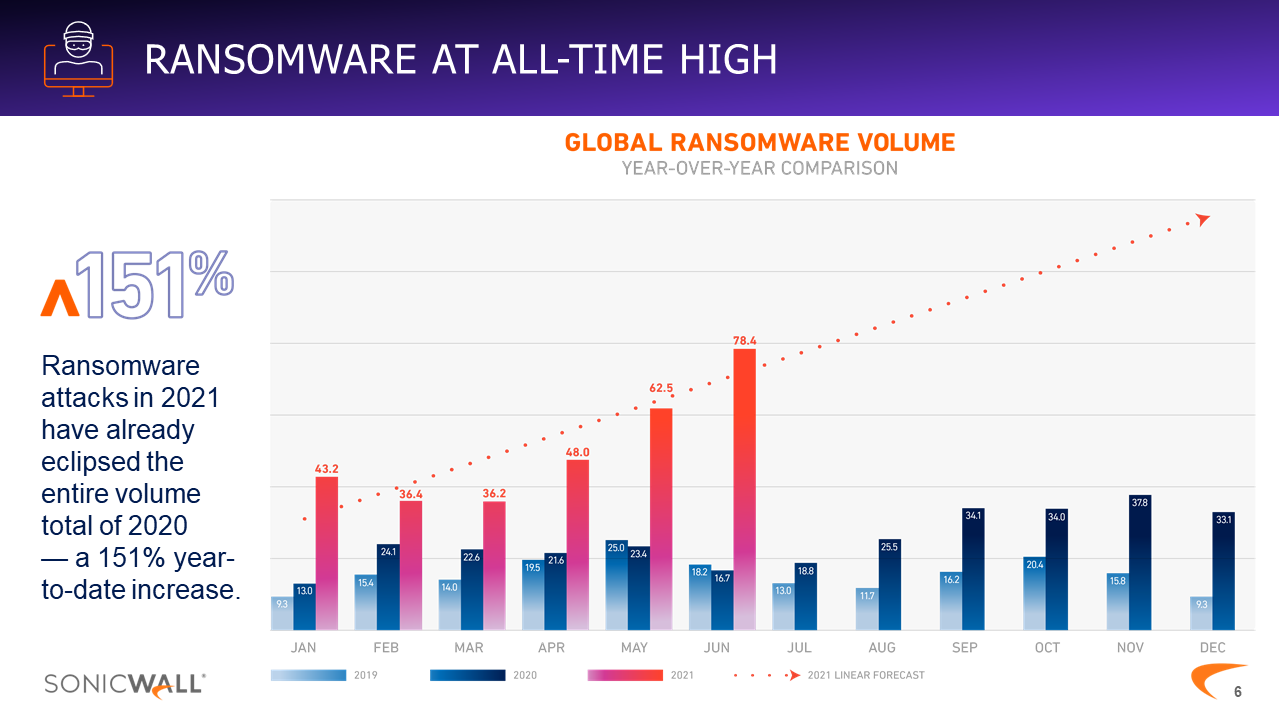
In fact, ransomware attacks have increased by 151% in 2021 — and the year isn’t over yet!
Asa you can see, ransomware attacks are only expected to get worse. And we can see the evidence in local news headlines:
- $40-million Ransomware Attack on Broward County Schools
- Access to Virginia government contractor sold by Russian cyber criminals
- “Team Snatch” demands ransom; leaks contractor information on the dark web
- DISA data breach exposes personal information of 200,000 people
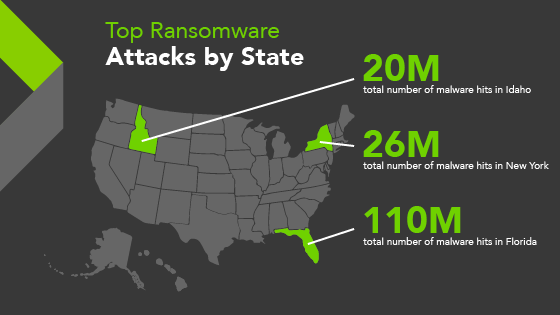
And unfortunately, Florida is winning a game nobody wants to play. We’re currently the top state for ransomware attacks at 110 million hits.
But that doesn’t mean hacks are inevitable. With the right resources, businesses can protect themselves.
Recommended Cybersecurity and Risk Management Services
Cybersecurity has to be comprehensive to be effective. Anti-virus software, alone, isn’t enough to stop hackers. But it’s a great start. Here’s what else businesses should consider for true protection.
1. Endpoint Detection and Response Software (EDR): Threats are detected and blocked on PCs and servers in real-time.
2. Managed Detection and Response Software (MDR): When threats are detected, the machine is disconnected from the network to stop any spreading
3. Threat Hunting Data Retention: If a threat is detected and damage is caused, logs are kept for a certain time period.
4. Firewall Management: Firewall software is regularly updated, ensuring all security settings match current standards and access remains secure.
5. Secure Local and Offsite Server Backup: Regular snapshot backups of your servers are taken and recorded, then securely uploaded to an offsite location.
6. Server Backup Verification and Test Restoration: A regular test restore of offsite server backups is performed to ensure backups are always retrievable.
7. Web Filtering Protection: A web filter that continuously scans desktops, laptops and servers for harmful websites — even when not connected to the office network.
8. PC DNS Monitoring: DNS (domain name system) settings control how websites on your computer are accessed.
9. Windows Server Security Updates: Servers are regularly improved with the latest security updates
10. Windows PC Security Updates: PCS are regularly improved with the latest security updates.
11. Common Desktop Application Security Updates: Common desktop apps like Microsoft Office, Adobe Acrobat and Java are regularly improved with the latest security updates.
12. Technology Risk Assessment and Roadmapping: Inventory PCs, servers, network equipment and operating systems to mark which outdated tech needs to be replaced and how to get from A to B.
13. PC Disk Encryption (Windows and Mac): Encryption management and activation in the case of lost, stolen or hacked computers.
14. Password Policy Management: Management of employee domain password policies such as password length, complexity and age.
15. Penetration Testing: Ethical hacking attempts are performed to find system weaknesses. This safe process ensures that any security gaps are fixed before they’re exploited.
16. Mobile Device Management: Mobile devices are set to only allow authorized apps and activity. This prevents rogue downloads that can invade your network.
17. Windows / Office 365 Account Monitoring and Security: Monitor accounts for suspicious activity. This includes unauthorized account changes, password policy violations and account lockouts.
18. Security Awareness Training: Regular security training to help employees identify potential threats, including phishing and social engineering.
19. Multi-Factor Authentication Software (MFA): Installed to ensure only authorized people can access computers and/or accounts. MFA sends a notification to your phone to approve device access.
20. Dark Web Monitoring: Scan the dark web (marketplace for stolen information) for personal information tied to your key staff members, business and personal email addresses.
Final Thoughts on Cybersecurity
In simple terms, the best solution for cybersecurity and risk management is to:
- Make security a standard, not an add-on.
- Invest in the right IT security partner
- Don’t want until it’s too late
- Never settle for bare minimum protection
You’ve built your business’ reputation, don’t let thieves behind a computer destroy it. iVenture’s award-winning team delivers managed services, cloud and cybersecurity to Florida’s best businesses. With statewide coverage, our offices in Jacksonville, Orlando, and Tampa make us your local IT partner. Whether you need end-to-end IT or a boost to your internal IT team, we’re ready. At iVenture, we give you more time to do what matters most.