As internet users, we’re all aware that sometimes the web isn’t so safe. No doubt you’ve heard of common cybersecurity risks like malware and phishing, but those aren’t the only threats to your data.
We’re taking a look at some weird, little-known cybersecurity risks that can impact you. As you use the internet, keep these threats in mind and be cautious when visiting websites and clicking links.
What is an SQL Injection?
Pronounced “sequel,” this type of cybersecurity attack uses computer code to infiltrate your system. SQL is a computer language programmers use to access their company databases.
For example, a clothing company will have a database of customer information, including names, addresses, phone numbers and more. Using SQL queries (AKA directions), programmers can command the database to show, update or remove records. This makes it easy for businesses to keep their information organized and retrievable.
Here’s the problem: hackers can use SQL queries too. A bad actor can execute a SQL injection, meaning input their malicious code into your website code. This allows them to access personal information from your database such as social security numbers, bank routing numbers, medical records and the list goes on.
Second-order SQL injections
These attacks follow the same method as SQL injections, but are designed to run at a later time, not immediately. You can have a SQL injection waiting in your code and not even know it.
What to Do
Install a firewall on all computers used by your business. Firewalls protect computers from unauthorized access by blocking the network. This means hackers won’t be able to manipulate your website code or worse, your information database.
It’s also a best practice to validate, or write code that identifies suspicious user inputs on your system and prevents them from entering into the system. This way, any hacker who attempts to input malicious code will be stopped from doing so.
What is a Drive-by Download?
As the name states, drive-by downloads happen passively. When you visit a site, malicious code can be waiting to jump on for a ride — even if you don’t click or download anything! This is what makes drive-by download attacks so sneaky. You may not realize you’ve got an unwanted passenger until it’s too late and your computer is infected.
What to Do
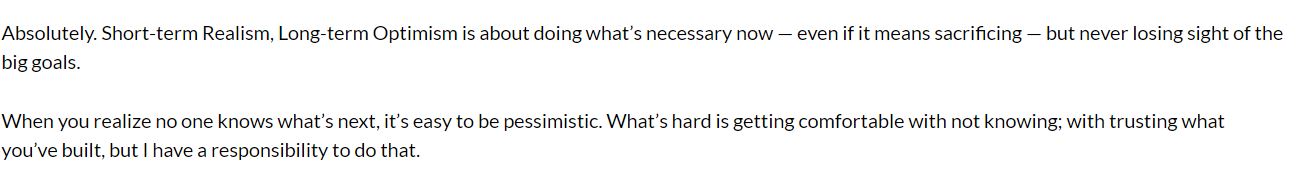
Drive-by download protection is simple in theory. Don’t visit dangerous sites and you’ll be okay. But how can you tell if a site is dangerous? Your internet browser may warn you beforehand like this:
Drive-by downloads mostly happen on seedy sites, but trusted sites can be compromised too. Common sense prevails with this type of cybersecurity risk. Always implement quality security software on your computers.
What is a Man-in-the-Middle Attack?
A twisted version of monkey-in-the-middle where the hacker is intercepting your communication with another website (unbeknownst to you). With man-in-the-middle attacks, you can get hit two different ways: via man-in-the-browser and network vulnerability.
Man-in-the-browser
With this method, bad actors attempt to put malware on your computer, often through phishing scams. You’ll be sent an email from a seemingly reputable source asking for information from you.
Once you click the link, the malware begins downloading. When you type in your information (name, address, credit card number, etc.), that malware is secretly recording everything you type. Hackers can abuse or sell that data on the black market.
Network vulnerability
If you don’t know about the dangers of public WiFi, read this. Using unprotected WiFi networks, like at Starbucks or even your own house, hackers can search the router for weaknesses that allow them to hack into the system.
From there, hackers can intercept, read and record the data you’re transmitting from your computer to the internet.
What to Do
Use public or unsecured WiFi networks cautiously. If you must use one, try not to visit any important websites like your bank or credit card site. Installing a virtual private network app is highly advised. To prevent man-in-the-browser attacks, set up an external email reminder for your staff like this:
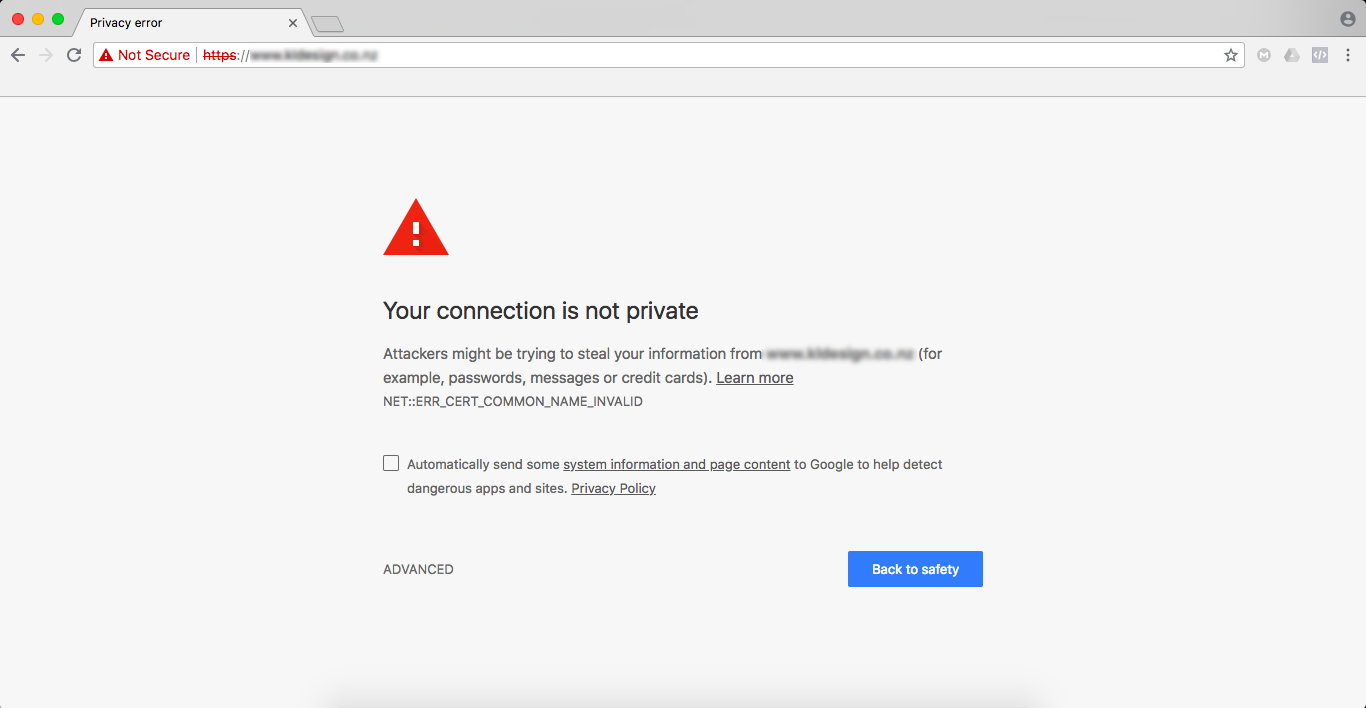
This helps everyone remember to practice caution with emails from outside sources. Instruct your team to contact the sender entity if they’re not expecting an email from them. Always looks for the HTTPS in website addresses. The “S” means the site is secured and safer than an HTTP site.
Safe
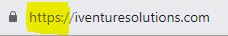
Unsafe*
*You’ll see that the Google Browser alerts you that this website isn’t HTTPS secure.
What is a Watering Hole Attack?
By now, you can tell the names of these cybersecurity risks describe the threats pretty accurately. Can you guess what the watering hole attack definition is? Hint: your business is the herd of zebra and the hacker is the crocodile.
With watering hole attacks, bad actors target a specific group, often employees of a company. They track this group to see which popular websites they all visit frequently, such as a business portal.
Once found, the hackers can do several things, including redirect the site to a fake malware-infected site or use drive-by downloading (see above) to infect many group members in one big attack.
What to Do
Watering hole attacks are difficult to prevent because they often use reputable, trusted sites (unlike most drive-by downloads). But you can do a few things to lower your chances of getting hit. These include:
- Keeping your computer software updated
- Turning off automatic HTTP redirects
- Monitoring your network 24/7 for suspicious activity
- Ensuring your browser is using the newest version
The internet can be a scary place when you don’t know what’s out there. But with awareness and a proactive defense plan, your business will be better prepared. Working with a qualified IT provider can help take the load off your back.
An MSP can monitor your networks, ensure all your software is updated, install cybersecurity tools like firewalls and create a plan to help your business combat threats. Let us do our job, so you can focus on yours.
iVenture Solutions is an award-winning managed service provider delivering superior IT solutions to clients across Florida.
As a leading-edge IT firm for small and medium-sized businesses, we provide a diverse range of services covering the entire scope of IT including maintenance, support, hosting and more.
Through rapid response time, reduction of chaos and the right people, our expert team of IT professionals will fulfill your technology needs. At iVenture, we give you more time to do what matters most.